Evolution of the Swift CSP since 2016
In an era where digitalisation has transformed the way financial institutions work, the security of financial data and transactions is more important than ever.
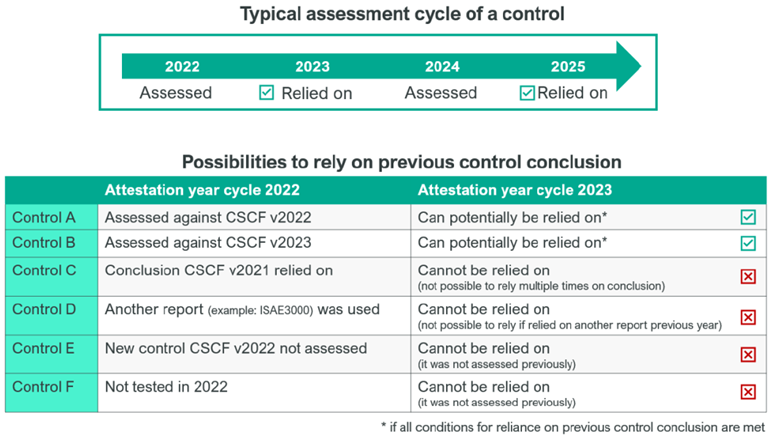
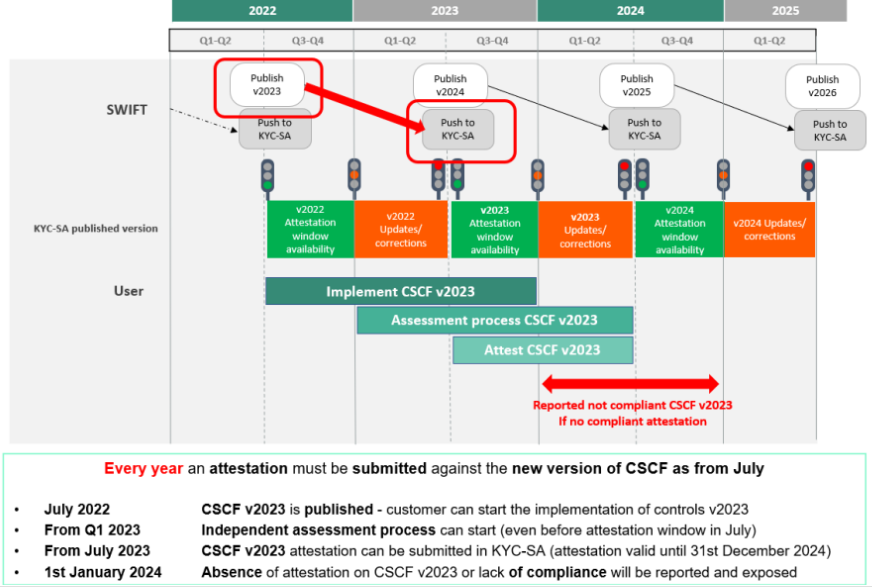
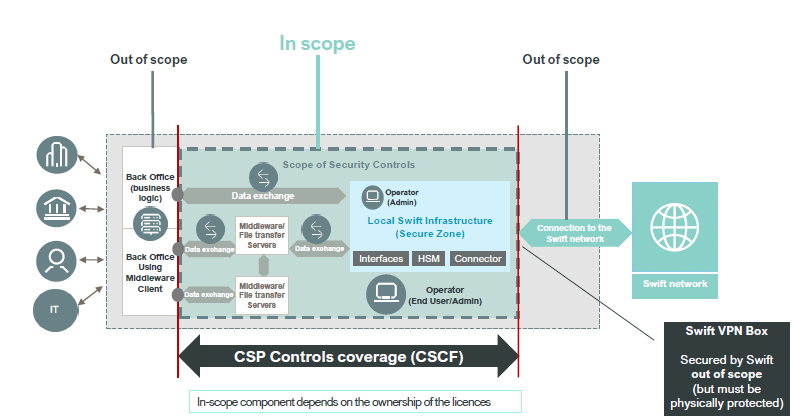
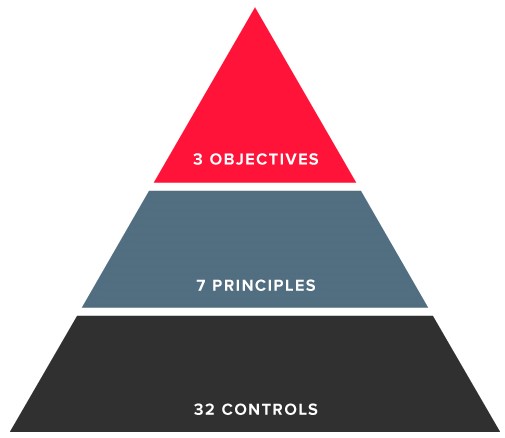
Following a number of security breaches at financial institutions, Swift became concerned about the security of its users. Swift decided to create a set of security controls and required all its users to attest their level of compliance with these controls transparently. The CSP is continually updated to address new threats and weaknesses in the ever-changing cybersecurity landscape.
 © by Swift 2024
© by Swift 2024
 © by Swift 2023
© by Swift 2023